Do Macs get viruses? Do Macs need antivirus software? The short answers are yes, and yes – but it’s a bit more complicated than that. In this article we look at the dangers faced by Mac users, and the pros and cons of using Mac antivirus software.
The Mac is generally considered to be safe and secure, and there are a number of reasons why Macs are considered more secure than PCs. Malware writers are less likely to target Mac users because of the perception that it has a far smaller market share than Windows. There is also the fact that the Mac operating system is Unix-based, and Unix offers a number of security features built in.
In addition, Apple has included a number of security measures that make attacking a Mac particularly challenging. These include Gatekeeper, which blocks any software than hasn’t been digitally signed and approved by Apple from running on your Mac without your agreement.
However, a security flaw was discovered in late February 2014 that means that an attacker could intercept your data if you are using your Mac on an unprotected hotspot, perhaps in your local Starbucks or an internet café.
Updated, 10 August 2016, to briefly discuss Apple’s new Security Bounty Programand what that means for Mac security.
Mac security FAQs: How does Apple discover security vulnerabilities in its products?
Apple has its own security research team, but it depends on users and independent researchers to help by reporting any flaws they find in Apple products.
To this end, Apple has an incentive programme that rewards such discoveries with payments of up to $200,000, depending on the seriousness of the flaw. But it was the last major tech company to set up such a scheme. (Microsoft set up its own bug-reporting incentive programme in 2013, and was itself criticised at the time for leaving it so late.)
On 4 August 2016, Apple security boss Ivan Krstic announced the Apple Security Bounty Program. “We’ve had great help from researchers in improving iOS security all along,” Krstic said. “[But] we’ve heard pretty consistently… that it’s getting increasingly difficult to find some of those most critical types of security vulnerabilities. So the Apple Security Bounty Program is going to reward researchers who actually share critical vulnerabilities with Apple.”
The top reward is $200,000, given to those who discover vulnerabilities in Apple’s secure boot firmware components; for less critical flaws the bounties drop through a series of smaller figures to a bottom tier of $25,000. Wired has the details.
We imagine most Mac users will be pleased to hear that Apple has finally launched an incentive programme to encourage more widespread reporting of its vulnerabilities. Incentivising security researchers to let Apple know about a flaw instead of passing it on to hackers (which may still, sadly, be more lucrative) makes Apple products safer for everyone.
Mac security FAQs: What is the KeRanger ransomware attack?
Ransomware is, in general, a sub-category of malware that involves dodgy software sneaking itself on to your computer and then encrypting files against your wishes. You’ll then be left with two apparent options: never be able to access those files again, or pay the ‘ransom’ to decrypt them. (Ransomware is one of the terms defined in our Apple jargon buster.)
For a long time ransomware was a problem that Mac owners didn’t have to worry about, but March 2016 saw the appearance of the first ever piece of Mac ransomware, distributed along with a version of a piece of legitimate software: the Transmission torrent client. Transmission has since updated to remove this malware (and Apple has taken steps of its own) but not before a number of unlucky users got stung.
If you want to make sure you don’t get caught out by KeRanger – and how to remove a range of other malware attacks -he Apple SSL bug, Gotofail error?
This caused issues for Mac users back in 2014. The problem was with Apple’s implementation of a basic encryption feature that shields data from snooping. Most websites handling sensitive personal data use SSL (Secure Sockets Layer) or TLS (Transport Layer Security), which establishes an encrypted connection between a server and a person’s computer so that snoopers cannot read the traffic and extract information like credit card numbers or log-in credentials. If an attacker intercepts the data, it is unreadable.
However, Apple’s validation of SSL encryption had a coding error that bypassed a key validation step in the web protocol for secure communications. There was an extra Goto command that hadn’t been closed properly in the code that validated SSL certificates, and as a result, communications sent over unsecured Wi-Fi hot spots could be intercepted and read while unencrypted. This could potentially expose user password, bank data, and other sensitive data to hackers via man-in-the-middle attacks. Criminals could also supply fake data that makes it appear an authentic web service has been cryptographically verified.
These kinds of attacks are known as a man-in-the-middle attack and it is a form of eavesdropping in which a hacker makes an independent connection between a client and its destination server. The hacker is then able to relay messages between them, making the client and server believe they are talking to each other over a private connection.
In order for this type of attack to be possible, the attacker would have to be on the same public network.
Apple quickly issued an update to iOS 7 and iOS 6, but took longer to issued an update for Mac OS X, despite Apple confirming that the same SSL/TSL security flaw was also present in OS X. Read more about the iPad and iPhone security flaw here.
Apple said it had a fix ready for OS X and would release it “very soon”. The fix came late the following night.
Mac security FAQs: How to update OS X 10.9.2
Apple issued a patch for the gotofail bug in an update to OS X Mavericks. Mac users running Mavericks were advised to update to OS X 10.9.2. OS X has since moved on to El Capitan, but checking regularly for OS updates remains a key part of a sound security strategy.
The 460MB-860MB update (depending on your system) patched the vulnerability along with 32 other vulnerabilities in Mac OS X. These vulnerabilities include six in QuickTime and four that could be used to bypass sandboxing. Sandboxing – a requirement for all apps sold in the Mac App Store – restricts apps from accessing files and data in other apps, as well as other network resources, protecting the user.
Along with the vulnerability patches in OS X 10.9.2, Apple also provided several non-security fixes to deal with reliability, stability and performance issues, as well as a few that beefed up some integrated features and tools.
Check if your system is up-to-date by clicking on the Apple logo in the top left of the menu bar. Then click About This Mac.
If you are still running a version older than OS X 10.9.2 head to the Mac App Store and click on the Updates tab. Wait while your Mac searches for updates. We had a couple of minutes of waiting before the new update showed up.
Once the update appears, click Update.
You will need to restart your computer once the update has downloaded. Our 460MB download took about 8 minutes (during which time we were still able to work) but then the restart and install took almost 20 minutes, bringing the total install time to about 25 minutes in total.
Mac security FAQs: Why did it take so long for Apple to fix the SSL vulnerability?
One theory is that Apple could (and indeed should) have fixed the vulnerability sooner but it was waiting until it was ready to get OS X 10.9.2 out the door – that update includes a number of new features including FaceTime Audio calls and call waiting. You can also block incoming iMessages from particular senders. There are also Mail patches and fixes included in the update.
Apple may also have concluded that since it is less likely that Macs will be used on a Wi-Fi hot spot it was less of a priority to fix the flaw on the Mac platform, the more popular iOS platform taking precedent. The flaw would only affect Macs being used on a public Wi-Fi network – but judging by our local Starbucks an awful lot of Mac users were put at risk.
Mac security FAQs: I can’t update my Mac – is my Mac safe?
As in iOS, the Mac OS X Mavericks flaw is limited to SSL connections over unsecured Wi-Fi networks, in Safari (Firefox, Chrome and other browsers are said to be secure.) However, other Apple and non-Apple applications are said to be affected, including Apple’s Mail, FaceTime, Calendar, Keynote, and iBooks. Third-party applications, such as the desktop Twitter application and possibly VPN (virtual private network) connections, are also said to be affected, depending on their configurations, according to Ashkan Soltani, an independent privacy and security researcher.
The danger is mitigated somewhat since an attacker must be on the same network as the victim. However, you could be open to attacks if you are using a shared network and someone is snooping on that network. This could be someone in your local Starbucks.
Secured Wi-Fi networks, such as home and business networks with encryption enabled, are not affected.
If you can’t yet install Apple’s fix here are some tips for using your Mac safely.
1. Don’t connect to public Wi-Fi networks.
2. The flaw affects any application on the Mac that uses SSL/TLS, including Safari, messaging apps and even Apple’s software update, so avoid using iMessage
3. Don’t use Safari. Use alternative browsers like Chrome and Firefox. The browsers Chrome and Firefox are not affected because they use NSS, which is a different set of cryptographic libraries for client and server communications.
Mac security FAQs: Other ways to protect your Mac
Despite the flaw descibed above, Apple Macs are generally a lot safer than PCs. As we mentioned at the beginnning of this article, there are a few reasons why Macs are more secure than PCs. One is the simple fact that malware developers are less likely to direct their attention to the Mac because of the perception that it has a far smaller market share than Windows. However, even more significant is the fact that the Mac operating system is Unix-based. Unix offers a number of security features built in, like the way that executable code and data is stored in separate folders (this is why deleting an app on a Mac is so simple).
In addition Apple has included a number of security measures that make attacking a Mac particularly challenging, these include Gatekeeper, which blocks any software than hasn’t been digitally signed and approved by Apple. If you try to open an app by a developer that Apple hasn’t verified you will see the message: “[this app] can’t be opened because it is from an unidentified developer.”
Read more about why Macs are safer than PCs here.
However, there are a few things worth doing to make sure you are completely secure when using your Mac.
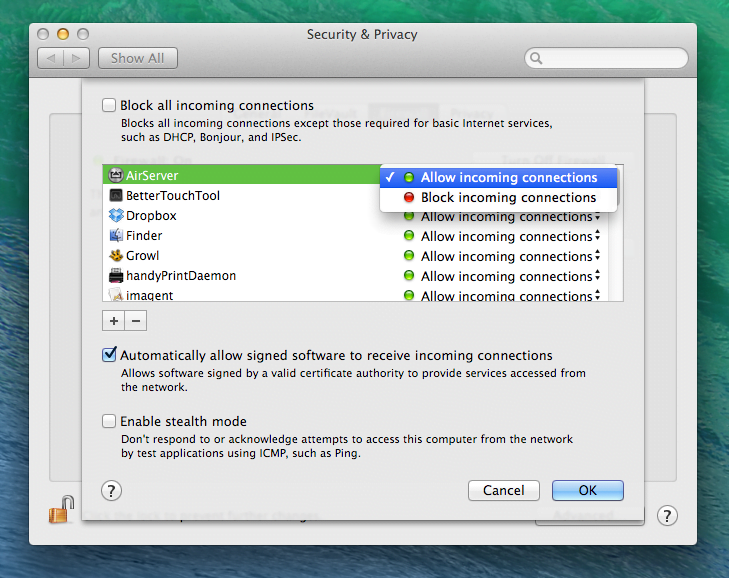
Mac security FAQs: How to turn on your Mac Firewall
The firewall defends your Mac against unwanted incoming connections from the Internet or other computers on the network.
Check to ensure the firewall’s enabled by opening System Preferences and selecting the Security & Privacy option. Click the Firewall tab and ensure it reads Firewall: On. If not, click the Turn On Firewall button. For fine-grained control over which apps are protected, click the Firewall Options button.

Mac security FAQs: How Apple’s Gatekeeper protects your Mac
All Macs running OS X Mavericks block downloaded software that hasn’t been digitally signed – a process in which Apple approves the developer. This leads to the familiar error message when you try to use or install unsigned software: “[this app] can’t be opened because it is from an unidentified developer.”
The system at work here is called Gatekeeper and can be controlled via the Security & Privacy section of System Preferences – select the General tab and choose from the options underneath Allow Applications Downloaded From. To turn it off, click Anywhere.
Setting this option to Mac App Store and Identified Developers is the best plan. All software downloaded via the App Store is signed, so you’ll only see Gatekeeper warnings with a minority of apps you’ve downloaded manually. You can bypass its protection when needed – assuming you’re sure an app or installation package is safe, just hold down Ctrl, then click it and select Open. This will mark it as being trusted.

Mac security FAQs: How to avoid Mac malware and viruses
If you download and try to open files contaminated with malware, you may see an explicit warning that the files will “damage your computer”, along with a reference to type of malware. You should delete the file immediately.
This protection is provided by XProtect, OS X’s malware scanning tool. This works invisibly and automatically in the background and requires no user configuration. Updates happen invisibly too.
Whether Macs need additional antivirus software is debatable but Sophos Anti-Virus for Mac Home Edition offers background virus protection for free, and iAntivirus by Norton, ClamXav and Bitdefender all provide on-demand scanning for zero cost, meaning you can run them whenever you feel it’s necessary to check for virus infections.
Mac security FAQs: Stear clear of Browser Plug-ins
Recent vulnerabilities with the Java and Flash plug-ins have highlighted the fact that there are cross platform threats that even Mac users need to be aware of. If there’s a major malware outbreak exploiting a buggy plug-in, XProtect will automatically disable it until an update is installed. Additionally, Safari in Mavericks lets you control what sites can use individual browser plug-ins. A policy of denying all sites plug-in access is a good one, unless they absolutely can’t function without them.
To set permissions, open the Preferences dialog (Cmd+comma) and click the Security icon, then click the Manage Website Settings button. Select the plug-in on the left, then click the dropdown alongside When Visiting Other Websites to set overall permissions, or select the site within the list to set individual permissions.
Avoid installing the Oracle Java Runtime software if you can but if you have no choice, or you’ve already installed it in the past, it’s a good to turn off its browser plug-in. To do so, open Java within System Preferences, click the Security button of the window that appears, and ensure there isn’t a tick alongside Enable Java Content In The Browser.

Mac security FAQs: Store passwords online with iCloud Keychain
Keychain is the OS X system tool that remembers usernames and passwords for websites, apps and even system tools like Wi-Fi.
With OS X Mavericks the Keychain data can be backed-up to iCloud, and also synced across any iOS 7 devices or Macs running Mavericks. This is clearly useful but raises security concerns. Apple says it uses “industry-standard encryption techniques” to store and transmit this sensitive password data, adding that the data “cannot be read by Apple”. Additionally, Apple never co-operates with government collection of data.
iCloud Keychain works in two slightly different ways, depending on whether you configure a security code while setting it up. With a code your Keychain data is backed up in iCloud. If you opt not to create a code, your Keychain data is merely synced across iOS devices and Macs. Backup in iCloud is a good insurance policy against theft of your device(s) or Mac(s).
To setup iCloud Keychain on a Mac, open System Preferences and click the iCloud icon. Put a tick alongside the Keychain box in the list. After entering your Apple ID password (not your Mac login password!), you’ll be prompted to enter a 4-digit numeric security code. To avoid doing so, or to if you worry a 4-digit PIN isn’t enough protection, click the Advanced button. For a stronger passcode consisting of a word, numbers, or even a whole phrase, click Use a Complex Security Code. To avoid a security code entirely, and thereby deactivate iCloud backup of keychain data, click the Don’t Create Security Code option.
Once you’ve entered a security code, you’ll be invited to enter a mobile phone number. Additional security codes can be texted to this number should you attempt to recover your iCloud Keychain in future.
To give a new device or Mac access to your Keychain, access iCloud via the Settings app in iOS (or via System Preferences on another Mac), then tap the switch alongside Keychain (or put a tick on the box on the Mac). Then click Approve With Security Code, and type your security code when prompted.
Alternatively, or if you opted not to use a security code, return to the iCloud panel of System Preferences on your Mac to authorise new devices or Macs. This can be done by clicking the Details button alongside the Keychain heading and entering your Apple ID password.

Mac security FAQs: How to get updates automatically
Mavericks can update automatically in the background – both system updates and any apps installed via the App Store. Bearing in mind hackers have been known to exploit bugs that get fixed via updates, enabling this feature is a good idea and can be done by opening System Preferences, then clicking the App Store icon. Ensure there’s a check alongside Automatically Check for Updates, and tick the three boxes beneath, which will enable downloading and installation of updates.
Some updates might require a reboot, in which case you’ll see a notification message telling you so. To view which updates have been applied recently, open the App Store app, then click the Updates icon.
Mac security FAQs: Do I need antivirus software for Mac? Should I install MacKeeper?
Whether Macs need an antivirus is still open to debate, but increasing numbers of Mac owners feel the need to install one – so much so that in 2011 one of the biggest Mac malware infections was via a fake antivirus app called MacDefender.
Another Mac antivirus company that is often thought of as unscrupulous is MacKeeper. There are various reports that suggest it is a scam or at worst malware. However, according to reports MacKeeper is not a scam, but unfortunately its aggressive advertising leads many to believe that it is, and perhaps it is unfortunately named (too similar to the fake antivirus app above). There are also complaints that it is difficult to uninstall.
There are a number of other antivirus software solutions for the Mac.
Sophos Anti-Virus for Mac Home Edition offers always-on virus protection for free, meaning that the app sits in the background and immediately alerts you should an infection take place.
Alternatively, iAntivirus by Norton, ClamXav and Bitdefender all provide on-demand scanning for zero cost, meaning you can run them whenever you feel it’s necessary to check for virus infections.
We look at the best options in our Best Mac antivirus software group test.

Mac security FAQs: Keep Java and Flash up to date on your Mac
Recent vulnerabilities with Java and Flash have highlighted the fact that there are cross platform threats that even Mac users need to be aware of. Over the past year Apple has taken to blocking Java and Flash via Xprotect. As a result of this you will find that from time to time Flash video and adverts disappear from your browser, and that Java based tools stop working.
[Source:Macworld]